Dark endpoints: an invisible threat to your IT team

Invisible devices create significant blind spots that can leave IT departments helpless to act against a breach until it is already too late. A new report from Absolute found 13% of enterprise devices aren't connected to the corporate domain.
The Absolute platform delivers self-healing endpoint security and always-connected IT asset management to protect devices, data, applications and users — on and off the network.

The Internet of Things: Risks & Mitigation Strategies

8 LOLBins Every Threat Hunter Should Know

Endpoint Security Risks in your Organization and how to overcome them

The Dark Web: How to Access and Potential Risks - CrowdStrike
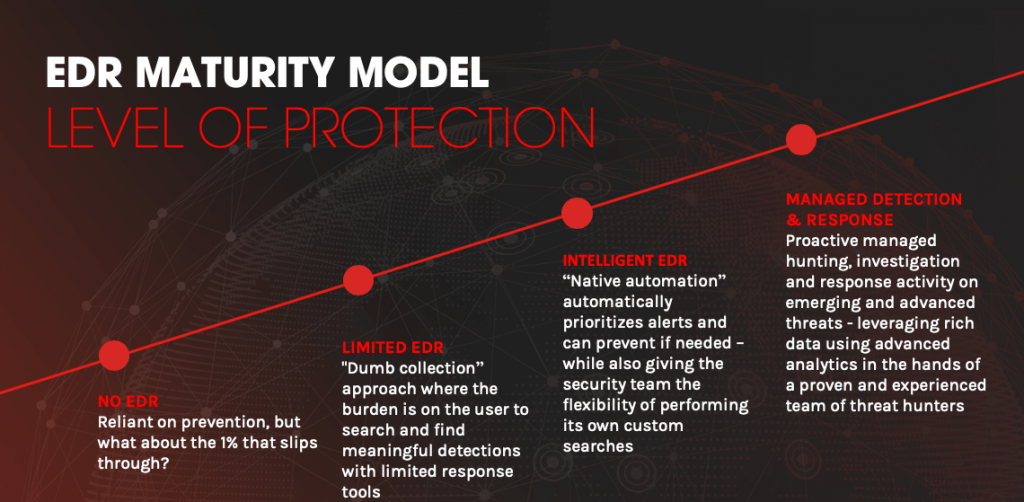
What is EDR? Endpoint Detection & Response Defined
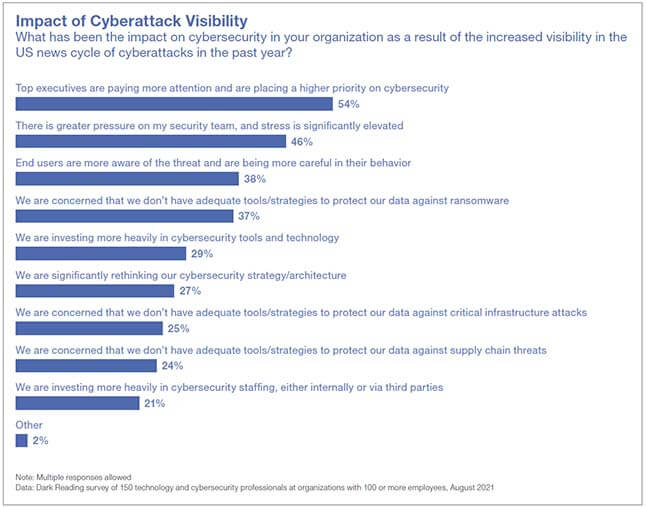
High-Profile Breaches Are Shifting Enterprise Security Strategy

EPP vs. EDR: Why You Need Both - CrowdStrike

Cybersecurity Threats Affecting Businesses in February 2024

What is EDR? Endpoint Detection & Response Defined

What is EDR? Endpoint Detection & Response Defined

Forescout Technologies Inc.

Enemy Unseen – Part I: How the Dark Web is Shaping Cybercrime

How to Make Cybersecurity Effective and Invisible









